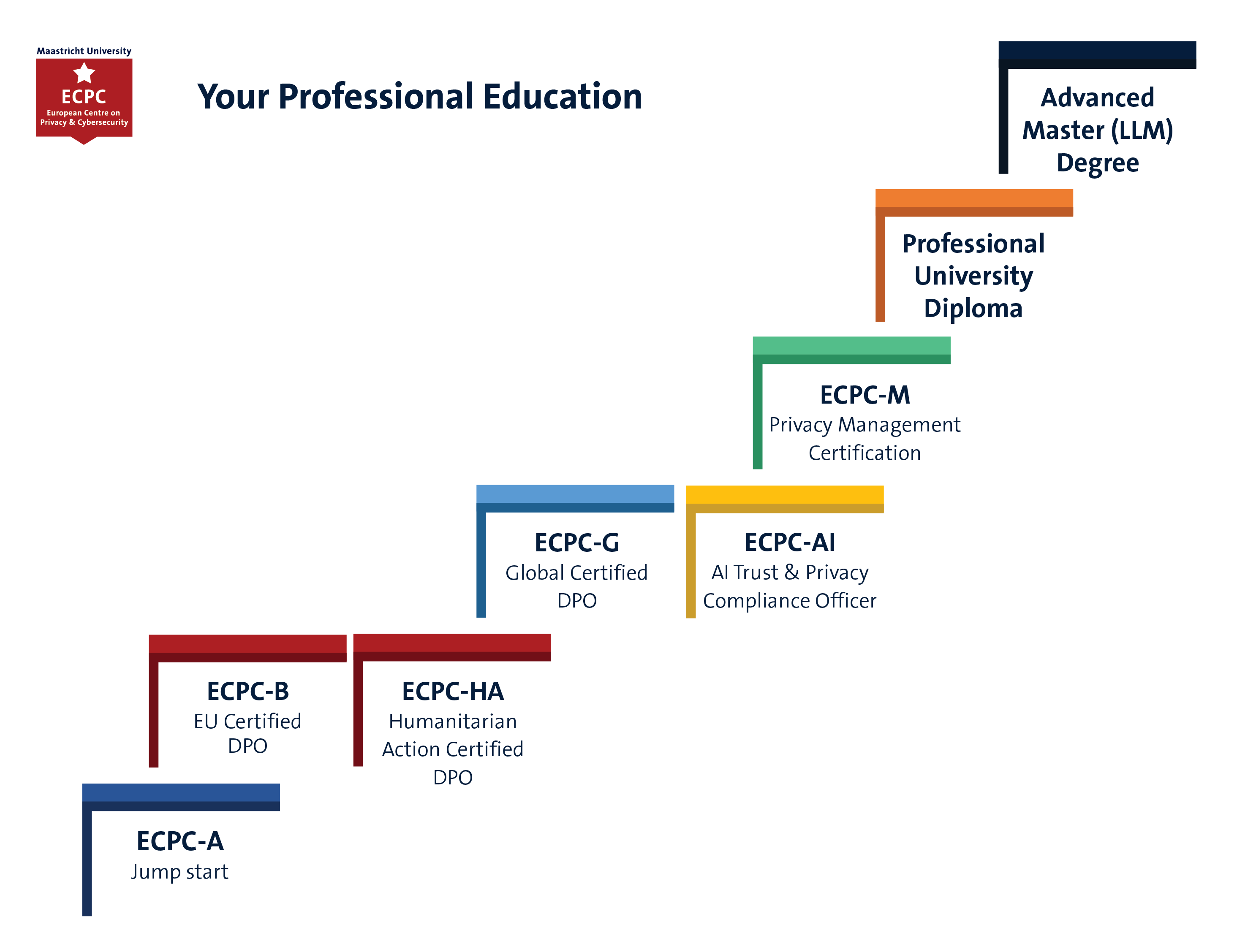
ECPC- Professional Certification Education
From a Maastricht University Certificate to your Master Degree …. plan your learning journey here!
Whether it is a Professional Certification or even a Master’s Degree... we believe your training does not stop at the end of a course. Obtaining a professional qualification from Maastricht University is only the beginning.
We offer you a continuous assessment and monitoring of your knowledge, skills and learning needs and a platform to keep on developing yourself. Holding and updating a Maastricht University certificate or professional diploma guarantees a strong asset in the fast-changing market where you need to act.
Fast facts
- Create your own learning track
- Pool of knowledgeable experts
- Obtain a professional certification
- Master on Privacy and Cybersecurity for professionals